The entire concept of Low-Code and No-Code development revolves around enabling rapid deployments of applications. This is why the Low-Code platform market is bound to reach $27 billion by the end of 2022. It is a suite of ready-to-use elements or components that you can leverage to create fully-working business applications.
This has attracted several businesses to reduce their time-to-market and quickly transform their ideas into applications. Research conducted by Forrester indicates that 84% of enterprises have already adopted Low-Code platforms for their application development needs. While many organizations believe that Low-Code/No-Code is far more secure than the technologies such platforms replace, some concerns can’t be ignored.
Low-Code development platforms have enabled several non-technical and citizen developers to develop new applications quickly. Along with the Low-Code development, businesses are also highly inclined to ready-made apps and solutions since Elluminati stated that it can increase revenue up to 85%. During the pandemic, it also assisted various organizations to develop business applications in lightning-fast development cycles.
At the same time, Low-Code development vendors need to ensure reliable security for their products. According to a study conducted by Gaurdicore, 76% of respondents did not have the necessary infrastructure to secure new apps or configure existing ones quickly.
Here, we will discuss Low-Code and No-Code development security concerns with practical solutions.
Significant Low-Code and No-Code development security concerns
Before discussing security concerns and their solutions, one of the essential aspects of Low-Code and No-Code developments is the terminology. First, there is no such thing as “No-Code”, as, without code, there is no application. It is like the atoms in a body, and the term No-Code symbolizes code hidden from developers in the form of modules or components.
Secondly, Low-Code means that you don’t need to write a hundred lines of code for application development. It is why such an approach is so attractive for small business owners without technical knowledge. However, there are security concerns which you need to keep in mind while using a Low-Code platform.

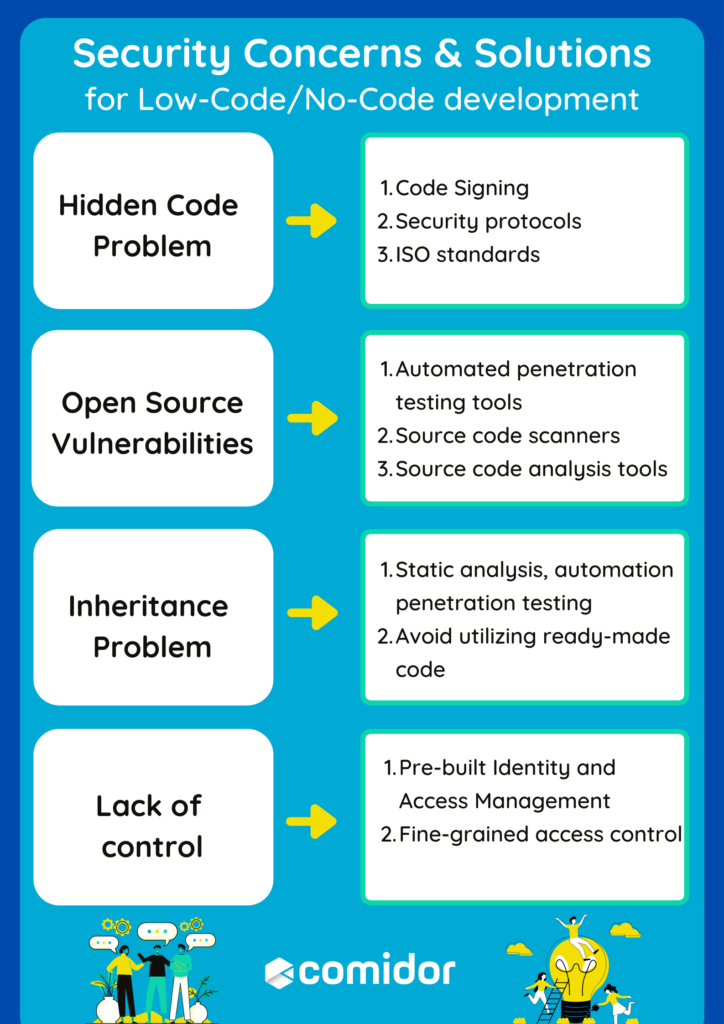
Hidden Code Problem
With the “No-Code” concept, the biggest part of the code remains hidden, a massive problem for developers. In addition, due to malicious attacks, there can be changes in the application code that will not be visible to the developers to rectify quickly. This means there is no way to know when or how a cyber-attack may impact your applications.
So, what’s the solution to this issue?
First of all, Code Signing plays an important role in all businesses to verify the applications built and used and increase trust and security. Authentication practices, public-key cryptography technologies, and digital signature mechanisms are used to ensure that the code has not been modified since it is signed. This way, businesses verify the authenticity and integrity of the hidden code.
So, you can either choose a vendor with a pre-installed Code Signing certificate with their service or buy a separate Code Signing certificate yourself from authorized providers.
The second thing, that you should do is to ensure that the Low-Code tool has security protocols in place. These protocols define secure access to data and enable protection against several cyberattacks. One of the most commonly used security protocols is the Secure Sockets Layer (SSL). This certificate enables encryption of sensitive data being sent between two systems and verifies the authenticity of the Low-Code tool details. For example, when a website is secured with an SSL certificate, HTTPS (HyperText Transfer Protocol Secure) appears in the URL.
What’s more, organizations that are certified to ISO 27001, comply with cyber security laws and other business, and legal requirements. This certification protects your organization and makes sure that your information security management system is efficient and effective.
Open Source Vulnerabilities
Modern software solutions rely on several open-source technologies. Unfortunately, with such frameworks and technologies, there are massive security concerns. According to a survey, 75% of unmanaged open source components had security vulnerabilities, with 49% of them showering high-risk exposure.
Most Low-Code platforms leverage such frameworks with ready-to-use open source components, which can pause massive security concerns. However, based on the Future of Open Source Survey 78% of enterprises embrace open-source software. Because of the large number of open source components used in software solutions, Low-Code software vendors rely on highly skilled security teams and developers that utilize tools that track the open source components and their security status.
Automated penetration testing tools and source code scanners enable software vendors and their teams to ensure security in the development process from start to finish.
What’s more, source code analysis tools, commonly known as Static Application Security Testing (SAST) tools, can assist uncover security problems by analyzing the source code or compiled versions of the software. These tools contribute to the detection of risks in the initial stage of software development, without breaking builds or exposing vulnerabilities in the application’s final release.
All in all, businesses need to invest in a reliable Low-Code solution vendor that follows certified safety procedures and identify open source risks before appearing in the production.

Inheritance Problem
The biggest Low-Code and No-Code development security concern is how applications or software are developed through reusable code. This code can be insecure and reused by beginner developers without in-depth knowledge or even access to the source code. So, the security issues and vulnerabilities in the base code are present in the new application as well.
Developers have access to stable and trusted code and they are able to employ code from those libraries as building blocks in their own software. However, code needs to be secure before being reused. Credible vendors guarantee that the code is secure in a number of ways, ensuring availability, fault tolerance, and recoverability.
As we analyzed above, security methods like Static analysis and automation penetration testing enhance the overall code quality and help in the detection of critical vulnerabilities.
At the same time, with Low-Code solutions, if users don’t prefer utilizing ready-made code, they can always write their own code and enhance the platform’s functions.
Lack of control
Most of the Low-Code platforms allow developers to quickly develop mobile applications and software without much coding and higher flexibility. However, access control becomes a massive problem. For example, an enterprise-based software or application has an access policy across platforms that allows developers complete control of the system.
At the same time, Low-Code platforms offer complete access control to users, which is a problem for developers looking to make quick changes for security purposes.
The first and probably one of the most effective solutions to this problem is to choose a reliable vendor offering all the security measures pre-built in the development tool. For example, if you are leveraging a Low-Code development tool that is cloud-based, choose the vendor that comes with pre-built Identity and Access Management (IAM). It will ensure a secure codebase and management of access control for your application. The fine-grained access control is a more comprehensive way to use parameters to determine who can and cannot access certain data, and resources based on business role, user, or department. This method of controlling access and application rights is of paramount importance especially when companies deal with huge amounts of data. Ensure that the Low-Code solution offers administration capabilities to manage users and their application rights to sensitive information, monitor the system’s health and status, and allocate resources depending on business roles.
 Conclusion
Conclusion
A Low-Code and No-Code development approach is an excellent option when you are looking for rapid deployments and digital transformation of business operations. However, you need reliable security measures to ensure that there are no disruptions and data breaches. The best way to ensure that your Low-Code platform has all the necessary security measures is to analyze different vendor services and choose the most secure one.
Building secure Low-Code applications with Comidor
Comidor is the best Low-Code choice to accelerate the development of secure applications. Throughout the application development and delivery process, Comidor meets multiple security standards for compliance and data privacy, offering the end-user a genuine experience without security concerns.
By integrating a full stack of security policies and services, Comidor Platform offers end-to end-security for cloud, data, and applications. Contact us to learn more.
Turn fresh ideas into powerful, secure Low-Code applications





